Categories
BaQapp Ransomware and Malware News
If you want to be notified of new threats and scams with defence updates, sign up for our newsletter above.
-
Vaulted or protected storage
Your backups must be protected through properly configured NAS – Network Attached Storage – where your backups are isolated from your network and safe from infection.
Ransomware will spread and infect network connected computers, external USB and thumb drives that appear as 'mapped' drives - drives with letters D,E etc. - even network file shares and cloud drives that appear as network drives. Ransomware will infect system files, Windows volume shadow copies (VSS) or System Restore functions you might believe offer backup safety.
BaQapp backs up files and disk images over your LAN to its local server using BaQapp's unique Debian Linux network protocol, providing a different OS environment. This "hardened" OS environment makes it extremely unlikely that ransomware will be able to deliver their "payload" or attack.
Versioned or incremental backups
Your backups must be versioned, so that each backup does not replace previous one, so should your recent one been infected, you must be able to go back to before the infection.Independently verified backup reports
Your backups need to be monitored or confirmed independently of your backup software to ensure that they are not missed.Automatic regular backups
Your backups must be automated and regular to ensure they are current. Very few users would be disciplined enough to be able to depend on manual backups



Care, know-how, updated software, good antivirus and luck might protect you against ransomware attack, but proper protected backups are the only 100% protection against ransomware extortion.
- Care
means being suspicious, checking and confirming the source before opening any special offers or gifts, post and courier notices, Amazon shipping confirmations, refunds, invoices, zip files, word files that ask to enable macros, celebrity news, disaster appeals, brand name vouchers, breaking news like Olympics canceled, unknown resumes, even links and payment requests from co-workers and bosses without confirmation. Never give out personal information even its just an email address unless you have confirmed its authenticity. Malware distributors (called agents) are often professionals who have all the time in the world to find your interests from corporate websites and social media, and then target you with ransomware that looks genuine. - Know-how
means keeping up to date on scams by subscribing to a site that sends info on new threats, which means reading time. - Diligence in downloading and installing software,
means that you should keep all your software patched and up to date so that you are less susceptible to attack through software flaws. - Antivirus helps,
but with 1,000 new malware versions a day, for anti-virus vendors to keep up to date is difficult. - Luck
because unless you have proper insulated backups using a product like BaQapp, your best chance is just to hope you are lucky, because there no 100% prevention and usually no fix for ransomware attacks. - The safest is to just ensure that you have proper backups
Get critical data stored in the cloud with versioning unless there are privacy fears. Dropbox will work.
Go for an enterprise level protection such as Shadow Protect, Veeam, StorageCraft, BackBlaze, Carbonite, CrashPlan and others that could be a bit costly and require an internet connection upgrade or consider BaQapp, the low cost onsite backup solution that offers vaulted, versioned, verified and automated monitored backups that comes with its own NAS from just $399.00, and no extra cost for multiple endpoints.
Speak to your technology consultant who may have some suggestions.
- Care
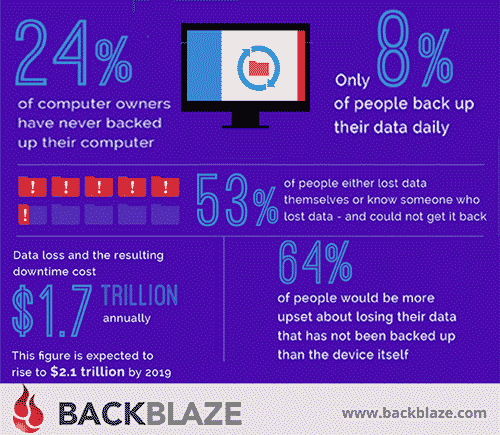
- Statistics and images supplied by BackBlaze.
- Expect many more attacks, since creating new or adapted malware is good business and the creator is exposed to little risk, charging up to $20,000 for effective Zero-day malware and ransomware on the Dark Web, while the distributor makes the big money but takes more risk.
- Half Of Our CEOs Fall Victim To Phishing Scams
- Firstly most phishing scams that target execs are well-crafted and researched. Similar-looking domains are registered and execs are carefully researched. Secondly, many execs have personal assistants who manage their day-to-day operations and who are often more susceptible to social engineering techniques.

- Attack on Australian accountants.
- "Accountants, only accountants, receive an email asking them to handle their affairs, and asking the accountant to review their portfolio before a planned meeting. The false portfolio is then emailed, but it contains ransomware" More
- FBI warned in late April.
- "Never before in the history of humankind have people across the world been subjected to extortion on a massive scale as they are today," security firm Symantec said in an August report on the subject. More
How fast does ransomware infect drives? If there's one thing ransomware authors love, it's shared network drives.
- Chimera: 18 seconds, Petra: 27 seconds, TeslaCrypt 4.0: 28 seconds, CTB-Locker: 45 seconds, TeslaCrypt 3.0: 45 seconds, Virlock: 3 minutes 21 seconds, CryptoWall: 16 minutes with 362,000 new crypto-ransomware variants spotted in 2015. That's an average of nearly 1,000 new variants every day.
Speed also becomes an important factor when you consider encryption isn't always confined to files on a single user’s machine. Many ransomware families we tested including the samples of Virlock, TeslaCrypt, and CTB-Locker also enumerate and encrypt network file shares. Ransomware campaigns like Samsam have shown an entire network can be compromised, with potentially catastrophic effects on an organization. That makes realizing just how fast ransomware encrypts files even more scary. Link to article Zero-day malware
- Zero day malware exploits vulnerabilities before they can be patched or protected by cyber defences. Zero-day malware which finds unknown weaknesses in software which are unknown to virus detection are the most dangerous.
Attackers are becoming more skilled at not only avoiding detection by vulnerability scanners, but also hiding from the automated analysis techniques that security firms rely on to detect malicious programs. - Expect many more attacks, since creating new or adapted malware is good business and the creator is exposed to little risk, charging up to $20,000 for effective Zero-day malware on the Dark Web, while the distributor makes the big money but takes more risk.
- Recent Zero-day exploits
- "Standard defenses are powerless against zero-day threats. Zero-day attacks are cyber attacks against software flaws that are unknown and have no patch or fix. FireEye has discovered 25 out of 40 zero-day exploits since 2013.
It's extremely difficult to detect zero-day attacks, especially with traditional cyber defenses.
Traditional security measures focus on malware signatures and URL reputation. However, with zero-day attacks, this information is, by definition, unknown.
Based on recently discovered types of zero-day attacks, operating system level protection is becoming less effective, and cyber attacks are becoming more sophisticated and better at bypassing organisational defenses." Link to FireEye article - "Most of the security tools are only effective against known threats,
- but many threats are built using zero day exploits that target vulnerabilities the software vendor isn´t even aware of." Link to original IT World article
- "Businesses ill-prepared to defend against dramatic rise in zero day attack
- The problem is that much of the conventional wisdom about security is reactive and most of the security tools available are only effective against known threats. The rise over the last year or so in targeted zero day attacks has left many organizations feeling defenseless and concerned." Link to Check Point report
- "The problem with traditional security solutions.
- Most security practices rely largely on regularly updating your operating system, software and antivirus tools, which are effective to protect yourself against known ransomware viruses — but are of no use against its unknown variants." Link to Tech Crunch report
- Adobe readies emergency patch for Flash zero-day bug
- "The zero-day vulnerability allows attackers to take complete control of a victim´s system." Link to original ZDNET article
- ‘Badlock’ Bug Tops Microsoft Patch Batch plus another Flash fix
- Microsoft released fixes on Tuesday April 14 to plug critical security holes in Windows and advice software. The company issued 13 patches to tackle dozens of vulnerabilities, including a much-hyped "Badlock" file-sharing bug that appears ripe for exploitation. Also, Adobe updated its Flash Player release to address at least two-dozen flaws — in addition to the zero-day vulnerability Adobe patched last week. Link to original Brian Krebs article
Articles offering advice on protection against malware, notably ransomware
- 8 Tips for preventing ransomware
- Backup - Don't enable macros - Install Microsoft Office viewers - Care opening unsolicited attachments - Limit log-ins - patch, patch - train everyone - segment network. Link to SOPHOS
- Meet the new ransomware that knows where you live.
- The carefully-crafted and user-specific emails contain links and personal information to trick victims into installing malware. Link
- Everything You Need to Know About Endpoint Security
- The way companies have been securing their endpoints for years — by installing antivirus — is now widely considered to be ineffective on its own. More information
- Ransomware on the rise, Australians among top targets
- As Australians, we love technology, we've got comparatively high disposable income, and we're almost always connected. Unfortunately, this has made our sun-drenched land the southern hemisphere's top target for ransomware, and attacks are on the rise. Link to original CyberShack article
- Ransomware Disguised as Windows Update Causing Havoc among Users
- After Samba ransomware that encrypts victims’ hard drives and CryPy ransomware known for encrypting each file individually here comes Fantom, a ransomware that uses full-screen Windows updates progress UI to get users to wait while it encrypts their files. Link to original article
- Personalised email attacks
- By sending the employees of a targeted firm a faked (or "spoofed") e-mail message that appears to come from a co-worker or other source within the company, a malicious hacker has a much better chance of persuading recipients to open an attached Word document than if the message appeared to come from a random sender. Link to original PC World article
- So you thought had to click on a virus to be ransomed.
- To mitigate it all follow standard best practices. Patch your servers. Have a backup.
New Ransomware installers can infect computers without users clicking anything. Ransomware infections have seen exponential growth in 2016, as both old encrypting malware like Cryptolocker and new versions like Locky are utilizing craftier methods to attack machines and encrypt files before victims even realize what's happened. Victims are then forced to either pay the ransom or hope they have a backup recent enough to spare them any lost data. Meanwhile, the time required to remove ransomware and restore lost files can prove costly as well. Link to original CyberShack article - Fortinet advises enterprises to take 10 critical steps against ransomware
- 1. Develop a backup and recovery plan to 10. Do NOT rely on employees to keep you safe (CRITICAL). See all 10 steps
- How to avoid becoming the next victim of ransomware
- "We have no computers to use. All our backups are encrypted!" See all 10 steps
- News broke that Prince Rogers Nelson was found dead.
- Internet criminals exploit celebrity death in a number of ways.
Be careful of scams with anything on anything related to Price's death: emails, attachments, any social media (especially Facebook), texts on your phone, anything. There are charity scams about the recent earthquakes in Ecuador and Japan. Do not click on any links in emails. Try this test. Link to phishing security test Safe Backup is the Best Defence against Ransomware
- Here's What I Learned After Being Attacked by Ransomware
- Backup your files: It is guaranteed to be the best line of defence.
More information - I watched in horror as my files in that folder were encrypted, one by one
- Within seconds, I could no longer open any of them. My laptop had been hijacked . . . by a KEYHolder ransomware virus. 1. Back, back, back it up. This advice comes directly from the Federal Trade Commission.
More information - A Dire Lack of Knowledge about Ransomware Exists Despite Record Number of Infections
- Of 5,000 PC-operators surveyed, merely 16% said they were scared of ransomware, while 43% stated they weren't even aware of ransomware. The way for end-users to defeat it is by possessing an active retrieval method along with certain dependable backup.
SPAMfighter News 30 May 2016 - More information - InfoBox researchers have observed a 35-fold jump in new domains created for ransomware.
- Portugal, the Netherlands, the United Kingdom, Iceland, and the Russian Federation, now collectively account for half of the malicious infrastructure.
More - Ransomware Should Never Succeed
- What's unbelievable about the ransomware epidemic is the number of successful attacks on business, government and others—a number that should be a big fat zero. If an IT department, consultant and cyber-security staff are doing their jobs correctly, all the data should be backed up on external systems or in the cloud. Then, if an infection occurs, restore the last backup. Moreover, critical data should be air-gapped—essentially stored on a separate domain that is off the network and inaccessible to attackers. The one thing that an organization absolutely should not do is pay the ransom. That only serves as motivation for cyber-gangs to step up assaults, and there's no guarantee that another attack won't occur. By Samuel Greengard 30 May 2016 - See more
93% of phishing attacks now have ransomware payloads
- Oh boy. Things have gotten from bad to worse in an awful hurry. The soft targeted phishing email targets people in a particular job category, but may include some customization, such as the name of the recipient in the salutation. Link to Stu Sjouwerman Blog - 4 June 2016
- Your Money or Your Data: 6 Ways to Protect against Ransomware Attacks
- 5. Cloud - Disk-based and cloud-based backup and replication methods promise enticingly short recovery times for your most critical data. But, even these methods can propagate corruption, especially if they overwrite changes to the prior backups. Verify that your backup process allows you to roll back (i.e., return) to a last-known good state of data prior to the corruption.
More information on protection - Finally, a tacit acknowledgement that networks provide neither the speed nor the capacity to handle the transfer of that much data to or especially from the cloud!
- Clouds are a service delivery model; they are not a storage technology in and of themselves. More information
- Bogus IT Security Company Websites that look just like the real sites from security software vendors like Symantec, McAfee, Malwarebytes, Kaspersky and others.
- When you search for these sites, you could easily pick the fake site instead of the real one.
These sites will then try to trick you into believing there is a new security software version you urgently need to install. But when you click the download button, a pop-up shows an 800-number claiming there is something badly wrong with your computer which needs to be fixed immediately before you download the new version. When you make that call, a scammer with a foreign accent answers the phone, demands remote access to your computer, and charges you a hefty credit card fee to fix an imaginary problem.
Only give out confidential information when YOU have initiated the call and never call numbers in an email that just appeared in your inbox. Only call a toll-free number that you know beforehand is legit, like on the back of your credit card, a statement you have received in the mail, or the order confirmation email you received at the time you bought the product.
More information from Stu Sjouwerman Locky is the first ransomware that was not an attached executable
- Locky has a macro script which then downloads the executable payload from a compromised website.
Additionally Locky comes as a targeted email with your name, even your address, harvested from social media or distributed through criminal activities.
Locky is the currently the most prevalent and profitable for criminals, often appearing as a request for payment addressed to you by name from an unfamiliar supplier, who may or may not have a website. The attachment is a Word file, also with your name as the title. Unless you enable macros, the software cannot attack (as at time of writing). Just delete the email and you may have saved yourself a great deal of grief. 
- If you did enable macros, you will very soon find all your Word documents encrypted and probably lost forever unless you have a insulated backup or you pay the ransom. If you have an attached hard drive which is not insulated as a backup, the files are likely to be also ransomware encrypted. Paying the ransom is an invitation to a later attack, but without backup, you may not have any option.
- "We received multiple Locky emails on 14 March, and they came straight through both my well known Virus defence software. By the next day the Locky emails were being flagged as malware. However on 12 and 17 April 2016 more were received, probably just with slight changes. Mail received through a Gmail account was effective at stopping Locky." Bernhard Kirschner Director BaQapp Pty Ltd.
- Excellent article on how Locky attacksLink to original blog site
- "You cannot rely on endpoint security tools with new attacks like this"
- Locky-ransomware-what-you-need-to-knowLink to original publication
- Locky was originally a malicious Word file.Link to original publication
- "Lately the Locky phishing email has a ZIP file attachment, possibly addressed personally, using a hijacked legitimate website."
- Easy to read article on CerberLink to Cerber article
- To protect yourself from spam e-mails, you have to look up the sender’s data. He could misrepresent a reliable company or entity. Spammers often write on behalf of national posts, courier firms, banks and government branches. They make the message look genuine by copying the contacts of the entity and registering a fake account which resembles its official e-mail address. If the message looks important, you can contact the organization to confirm its legitimacy. The malignant program uses AES-256 encryption technology to lock files.
-

Petya is another new ransomware, which arrives as a pdf attached to a resume.
- Petya is currently being distributed via Dropbox links in e-mail messages, as well as through email. The attachment throws up a Windows alert, and if you click continue, Petya is inserted into the master boot record (MBR) of the your computer, then restarts your computer. On reboot, the malware performs a fake Windows CHKDSK, warning "One of your disks contains errors and needs to be repaired," Petya then flashes up an ASCII skull and crossbones, announcing "You became victim of the PETYA RANSOMWARE!"
-

- It then displays instructions on how to obtain a key to restore the disk through one of two Tor (Dark Web) hidden sites. The attackers demand about Au$500.00 Bitcoins in ransom to restore the drive
- Petya is like opening up a filing cabinet, taking out all the carefully-filed papers, unstapling
- …and then throwing the whole lot high in the air to land in a jumbled up mess.
Link to SOPHOS publication - Petya ransomware leverages Dropbox and overwrites hard drives
- Using the cloud storage site to promote ransomware infections appears to be a new technique
Link to SC Security Magazine - One called Petya attacked the entire hard drive, and another called Jigsaw deletes files every hour the user fails to pay, but there are tools to reduce the damage, but you do need expertise to use them.Link to original publication
- Petya password generator, process is not something that everyone will be able to follow -- it is a little technical -- but it's worth persevering if you are caught.Link to original publication
- Eleanor Mac malware opens Tor connection for attackers to spy on and control Macs.
-

- Security researchers have discovered a nasty surprise hidden as a fake file converter application, called EasyDoc Converter, available on a number of download sites. The malware also uses a webcam control panel tool to capture images and videos from built-in webcams, as well as a daemon agent that collects infection information, fetches and updates computer files; and executes shell scripts, reported Bitdefender. It is mostly used in ransomware campaigns, point-of-sale malware and for botnet infrastructures - 8 July 2016. Read more
So you thought your Macintosh is immune to Ransomware. It is not.
- The first known ransomware attack on Apple Inc's (AAPL.O) Mac computers, was discovered in early March 2016, was downloaded more than 6,000 times before the threat was contained. Hackers infected Macs with the "KeRanger" ransomware which locks data on Macs so you cannot access it.
- Still, cyber security experts said they expect to see more attacks on Macs as the KeRanger hackers and other groups look for new ways to infect Mac computers. The 'Mabouia' malware for Apple's OS X now could pose a similar threat to Macs.
- The ingredients for criminals to attack Mac OS X desktop machines are here, according to Symantec, which confirmed that a tool "could be used to create functional OSX crypto ransomware". That is, if cyber criminals get their hands on it. How long do you think it will take before they do?
- First mac ransomware had sights on encrypting backups too
- First Macintosh ransomware encrypting more than 300 file types stored on a Mac's internal hard drive, had sights on encrypting Macintosh backups too, including any Time Machine backups. More information
- Watch out! There are Apple ID SMS phishers about!
- "Your Apple ID is due to be expire today"... yeah, right Link to Graham Cluley security advice
- Mac ransomware caught before large number of computers infected.More information
- KeRanger, which locks data on Macs so users cannot access it, was downloaded about 6,500 times before Apple and developers were able to thwart the threat
- Mac Users Attacked Again by Fake Adobe Flash Update
- Mac users are once again being urged to exercise caution when installing updates to Adobe Flash Player, after a fake update was discovered infecting computers. As been signed with a legitimate Developer ID certificate — effectively tricking OS X's built-in Gatekeeper security to believe that the files can be trusted and are not malicious. Posted by Graham Cluley
So you thought Linux was immune to Ransomware. It is not.
- Ransomware can attack Linux-based machines, specifically the folders associated with serving web pages. Called Linux.Encoder.1 the ransomware will encrypt your MySQL, Apache, and home/root folders and then asks for a single bitcoin to decrypt the files.
- Pay the ransom and hopefully the system receives a signal to traverse the directories again to decrypt the files. Link to TechCrunch article
- Cloud - njRAT: How can .NET malware be detected and mitigated?
- A Trojan called njRAT has emerged that is written in .NET rather than C/C++. Link to TechTarget - SearchSecurity
- Hackers ramp up ransomware attacks by encrypting your cloud storage too
- With KeRanger, hackers have started to code it to encrypt your local backed up files and, down the road, it could target the files you back up to the cloud. (Maybe soon, but BaQapp have not come across any proven instances - yet!) Link to clickjacking article
- Out-of-date apps put 3 million servers at risk of crypto ransomware infections
- More than 3 million Internet-accessible servers are at risk of being infected with crypto ransomware because they're running vulnerable software, including out-of-date versions of Red Hat's JBoss enterprise application, researchers from Cisco Systems said Friday. Link to arstechnica article
- Adobe Releases Emergency Flash Player Patch Against Ransomware Attack
- All operating systems including Windows, OS X, Linux, and ChromeOS vulnerable. This Cerber Ransomware is buried in ads on bad or malicious websites. Link to gPost article
- Adobe Releases Emergency Flash Player Patch Against Ransomware Attack
- All operating systems including Windows, OS X, Linux, and ChromeOS vulnerable. This Cerber Ransomware is buried in ads on bad or malicious websites.Link to gPost article
So you thought Android was immune to Ransomware. It is not.
- Simplocker was the first Android ransomware to actually encrypt user files.
- Android ransom-lockers Android/Lockerpin.A, prevents access to your device without root privileges, apart from a factory reset that would also delete all their data. The user will be prompted to pay a $US500 ransom for allegedly viewing and harboring forbidden pornographic material. Link to Simlocker article
- Android ransomware uses clickjacking techniques to trick users into granting it administrator privileges.
- Symantec claim that ransomware creators have created a new threat called Android.Lockdroid.E that abuses the different types of windows that Android applications can trigger. Link to clickjacking article
- Windows and Android users are increasingly experiencing ransomware attacks
- For these victims, the threat of losing sensitive data is greater than ever. Link to clickjacking article
There are many other dangerous ransomware strains
- TorrentLocker, CryptoWall and TeslaCrypt are just three variants of crypto-ransomware that have targeted Windows machines in Australia, locking up victims' files until a payment of around $300 is made. Having been around for some time, your virus detection software should protect you, until they come out with variations.
- A risk when attacked by ransomware is that if the ransomware distributor is shut down, and you do not have a safe or insulated backup, you cannot pay the ransom and your data is lost forever.
- Ransomware strain UltraDeCryptor simply does not deliver the unencryption routines after you pay.
- If you have no backups, you are truly hosed. Link to Stu Sjouwerman Blog - 4 June 2016
- There is even a tool that helps you identify 55 different ransomware
- 7ev3n, AutoLocky, BitMessage, Booyah, Brazilian Ransomware, BuyUnlockCode, Cerber, CoinVault, Coverton, Crypt0L0cker, CryptoFortress, CryptoHasYou, CryptoJoker, CryptoTorLocker, CryptoWall 2.0, CryptoWall 3.0, CryptoWall 4.0, CryptXXX, CrySiS, CTB-Locker, DMA Locker, ECLR Ransomware, EnCiPhErEd, Hi Buddy!, HOW TO DECRYPT FILES, HydraCrypt, Jigsaw, JobCrypter, KeRanger, LeChiffre, Locky, Lortok, Magic, Maktub Locker, MireWare, NanoLocker, Nemucod, OMG! Ransomcrypt, PadCrypt, PClock, PowerWare, Radamant, Radamant v2.1, Rokku, Samas, Sanction, Shade, SuperCrypt, Surprise, TeslaCrypt 0.x, TeslaCrypt 2.x, TeslaCrypt 3.0, TeslaCrypt 4.0, UmbreCrypt, VaultCrypt Link to ransomware tool
- Cerberis buried in ads on bad or malicious websites.
- Click an infected ad, and using an Adobe vulnerability, now patched, and it encrypted all of the data on your drive and demanded up to $1,000 to get it back. Link to Cerber Article
- Cerberis buried in ads on bad or malicious websites.
- Click an infected ad, and using an Adobe vulnerability, now patched, and it encrypted all of the data on your drive and demanded up to $1,000 to get it back. Link to Cerber Article
- CrypVault while not very sophisticated, still poses a major enterprise threat.
- A new variant uses the .vault extension giving the appearance it's already been quarantined. Link to CryptVault Article
- TeslaCrypt distributed on mass compromised networks onto the victim's machine.
- Takes files hostage with the use of encryption, with no assurance how to prevent attacks. Link to TeslaCrypt Article
- Reveton actors behind new CryptXXX ransomware. "Actor is the name given to a malware developer"
- Unlike other ransomware "written and/or distributed by less experienced actors" that failed to gain traction, the researchers said that "given Reveton's long history of successful and large-scale malware distribution, we expect CryptXXX to become widespread." Link to SC Magazine
- Russian Ransomeware Campaign Managers can do well
- The typical head of a ransomware operation makes about $90,000 a year for recruiting distributors and malware development, in just a few hours a week. More
- CTB Locker (Curve-Tor-Bitcoin) otherwise known as Critroni, CTB is a file-encrypting ransomware sold online for $3,000 USD, including support that targets Windows.
- CTB is a file-encrypting ransomware sold online for $3,000 USD, including support that targets Windows. Link to CTB Article
- CTB-Locker Ransomware Uses Bitcoin Blockchain to Store & Deliver Decryption Keys.
- Recently switched to targeting websites via a PHP version, first observed last February Link to Article
- Samsam attackers target unpatched server-side software using Jexboss
- Installs ransomware code directly, and compromising all connected computers. Link to Samsam Article
- Ransomware targets Dropbox users, overwrites hard drives, locks up their computer.
- Victims are linked to a resume on a dangers storage like Dropbox, but instead are hit with malware. Link to CRN Article
- New ransomware variant encrypts files using 7-Zip software
- The Nemucod version that contains this feature is distributed by spam mails pretending to be a court appeal - 22 April 2016
Link to myce article - Cloud - Resiliency in the cloud: myths versus facts Link to IBM paper on cloud resiliency
Breaking news on WannaCry ransomware
The first thing to do is to update your Windows Operating System through your own update option in Windows. Optionally you can use this link https://technet.microsoft.com/en-us/library/security/ms17-010.aspx.
Four Essentials for Proper or Strong Backup
Prevent ransomware extortion by Vaulted, Versioned, Verified and Automated backups.
BaQapp Ransomware and Malware Links
These articles have been selected from recent publications as a resource on current ransomware threats. Unfortunately too many users and journalists are not aware of the dangers to their data and the limitations of virus detection and backups that are not insulated.
BaQapp offers a safe insulated local data storage, that enables fast recovery from ransomware attack.
We update this page and our Facebook page regularly. If you want to be notified of new threats and how to defend yourself, just LIKE us on Facebook and you will be updated whenever we update our Facebook page.
We have selected some important links related to online security, ransomware and cyber protection.
BaQapp Threat Samples
BaQapp Pty Ltd works hard to keep up to date on threats to your data and storage.
We have selected some examples of emails or online security threats that you might experience. Click on an image to show the details of that threat (note that these are only images that demonstrate the threat - not the offending malware itself).
This page and others on this website are provided "as is" and are to be used for education information purposes only.
If you want to see the web address of a link, just scroll over the link and the source of the article will appear over the link.
Your best defence against extortion is care, knowledge with insulated, versioned, automated
and monitored backups done very effectively by BaQapp.

